
“What is the difference between a vulnerability scan and a penetration test?”
It’s something we are often asked by clients who are considering their security and starting to look at ways to protect themselves and their businesses.
Vulnerability scans and penetration tests are very common assessments that cyber security companies conduct – but if you don’t know the pros and cons of each, it is possible to waste time and/or money – and not get the desired results.
In this blog, we explain and explore the differences between the two approaches to help answer the question.
Firstly, lets explore the nuances between the two
Fundamentally, vulnerability scanning is focussed on identifying risks and helping prioritise fixes, whereas penetration testing focusses on exploiting vulnerabilities to determine the extent of damage an attacker could cause on an environment.
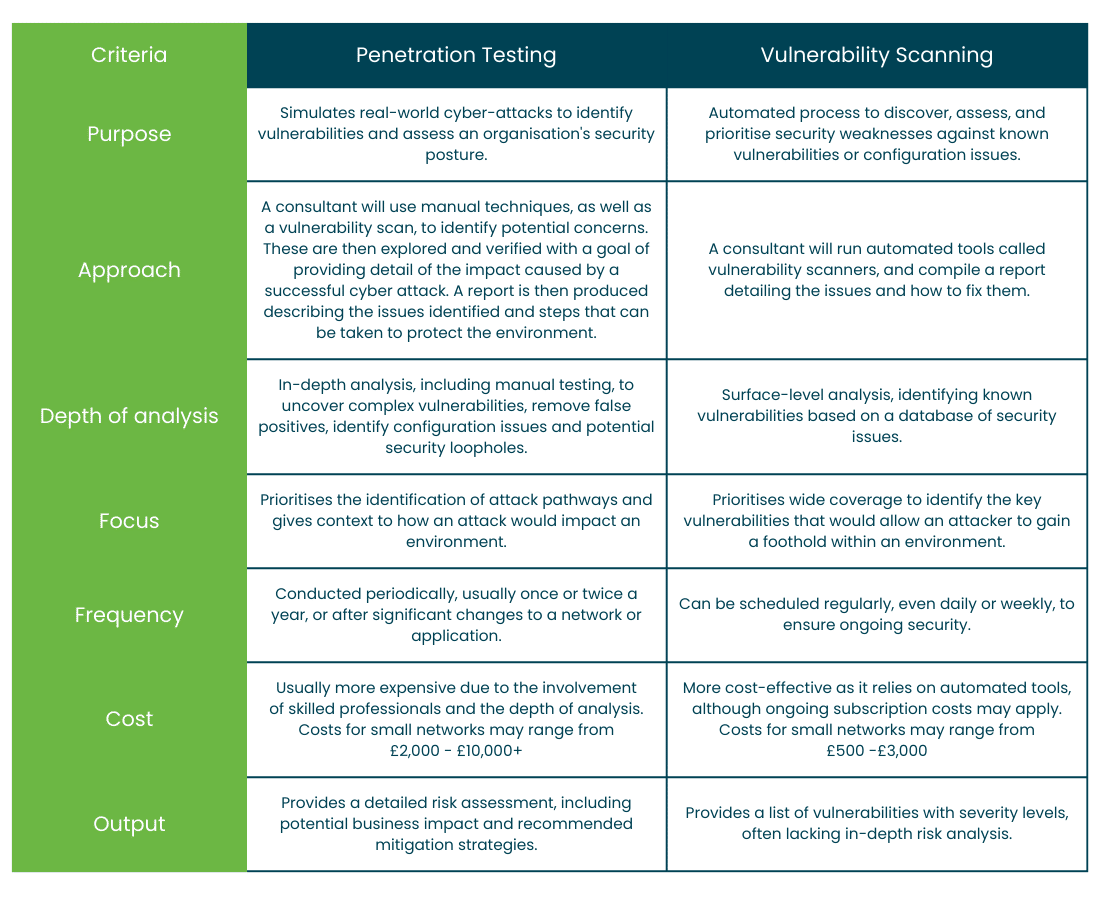
So, which one should I choose?
First of all, let’s consider the following:
- Are you obliged to undertake any specific kind of tests or testing (for example for insurance, regulatory or compliance purposes)?
- What is your budget?
- How sensitive is the data and information you hold on your systems?
- What level of detail are you looking for?
Ultimately, the type of assessment you choose to take depends both on the answers to these questions and your specific goals or business requirements.
For example, if you need real world insights and an understanding of how well your systems and/or data are protected and want to understand the likely attack method and impact of a cyber incident, then a penetration test may be right for you. This will help meet any compliance requirements, as well as ensuring you are protecting data.
Whereas, if you would benefit from more continual mapping of the vulnerabilities across an environment and want to be able to gather this information frequently to check systems are patched and protected from common issues, a vulnerability scan may be the right approach. This will allow you to have a more consistent view of security at a lower cost.
In summary
Don’t assume you have to pick one or the other.
Any company new to cyber security could start with vulnerability scanning as a first step and as their maturity or size increases, start to explore penetration testing.
Companies that are larger can choose to run these kinds of assessments in tandem to achieve a constant understanding of their security, as well as annual or bi-annual reviews to assess the impact of an incident.
If you would like to find out more about pentesting or other options to help protect yourself, from security assessments or awareness training to ongoing cyber support, then please get in touch.

How to Start Your Career In Penetration Testing
A HOW TO GUIDE If you want a career in penetration testing but don’t know where to start, this e-book will take you through what you need to know, with plenty of advice and tips throughout. Introduction Let's be honest. The cyber security industry is a mystery to most...

Crack more passwords with custom wordlists
Password cracking is an essential skill for penetration testers. Whether it is being used to crack a hash you’ve got from using responder, gain a first foothold on a device, or attempting to compromise accounts for lateral movement through a network, it is an...

What are JWTs – and how to ‘hack’ them
JSON Web Tokens – or JWTs – are a common method of providing authentication and authorisation to a web application. While they may seem complex, it is possible to look closely and break down the structure of these three-part tokens, to understand the different...

An A-Z of pentesting terms and abbreviations – Part 2
In this blog post, we continue our A-Z glossary of common pentesting abbreviations, acronyms and terms, from N-Z. Get ready for the likes of OSINT, RFI, YubiKeys and more. And don’t forget, you can catch up on any terms you missed in part one (A-M) here. N – Nmap One...





